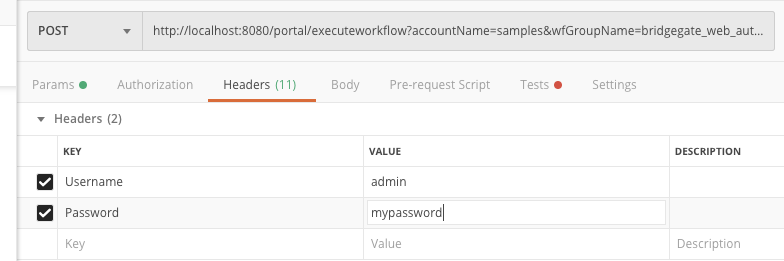
BridgeGate Web Service enabled as a service supports User/Password in the SOAP Header.
Authentication : This specifies whether Authentication should be performed and if so what type. NONE : No authentication will be performed by this BridgeGate Web Service.
BASIC : Choosing BASIC will reveal inputs for user name and password. These values will be stored in the workflow for comparison against values provided in the request as follows: (Note: do not confuse BASIC with “Authorization: Basic” BASIC in this scope is referring to the username / password being provided in the workflow) The BridgeGate Web service will use the inbound SOAP header to identify the username and password to use for authentication.
BridgeGate will look for 'Username' and 'Password' in the SOAP header. Example of Soap Header
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsd="http://mytest.bridgegateintl.com/websvcs/usertopersonservice/xsd">
<soapenv:Header>
<Username>admin</Username>
<Password>YWRtaW4=</Password>
</soapenv:Header>
<soapenv:Body>
<xsd:Root>
<xsd:User>
<xsd:Age>23</xsd:Age>
</xsd:User>
</xsd:Root>
</soapenv:Body>
</soapenv:Envelope>
The Username field is assumed to be plain text.
The Password field is assumed to be base64 encoded.
BRIDGEGATE : The BridgeGate Web Service will authenticate the values provided in the request against the BridgeGate Users as follows: The BridgeGate Web service will use the inbound SOAP header to identify the username and password to use for authentication.
BridgeGate will look for ‘Username’ and ‘Password’ in the SOAP header. (See above example)
The Username field is assumed to be plain text.
The Password field is assumed to be base64 encoded.
The username and password will be authenticated against the BridgeGate Users and the Users must have BridgeGate Web Service portal permissions.
Failed Authentication : Results in an AXIS Fault being returned with faultcode of “401” and faultstring of “Authentication failed : Username or Password is incorrect or User does not have security rights”. Either correct the Username and/or Password and resend your request or if doing BRIDGEGATE Authentication confirm that the user has the “BridgeGate Web Service” protocol permission.